Which of the Following Is Used for Biometric Authentication
The agency will continue to utilize mobile phones for identity. Government Agencies typically require AAL 2 solutions for access to official information systems and may require AAL 3 solutions for access to sensitive or mission critical information.
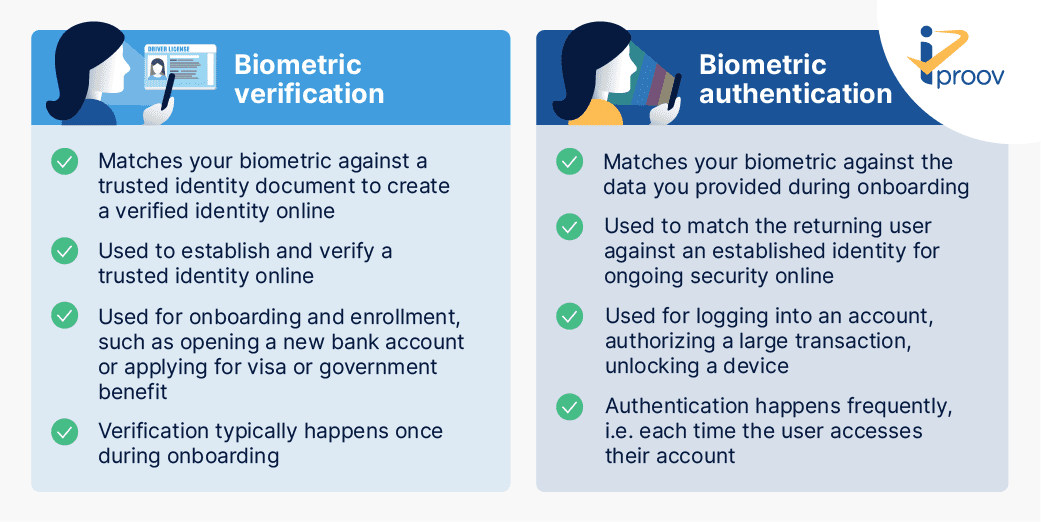
Biometric Authentication Vs Biometric Verification Iproov
The term applies to a vocal sample recorded for that purpose the derived.
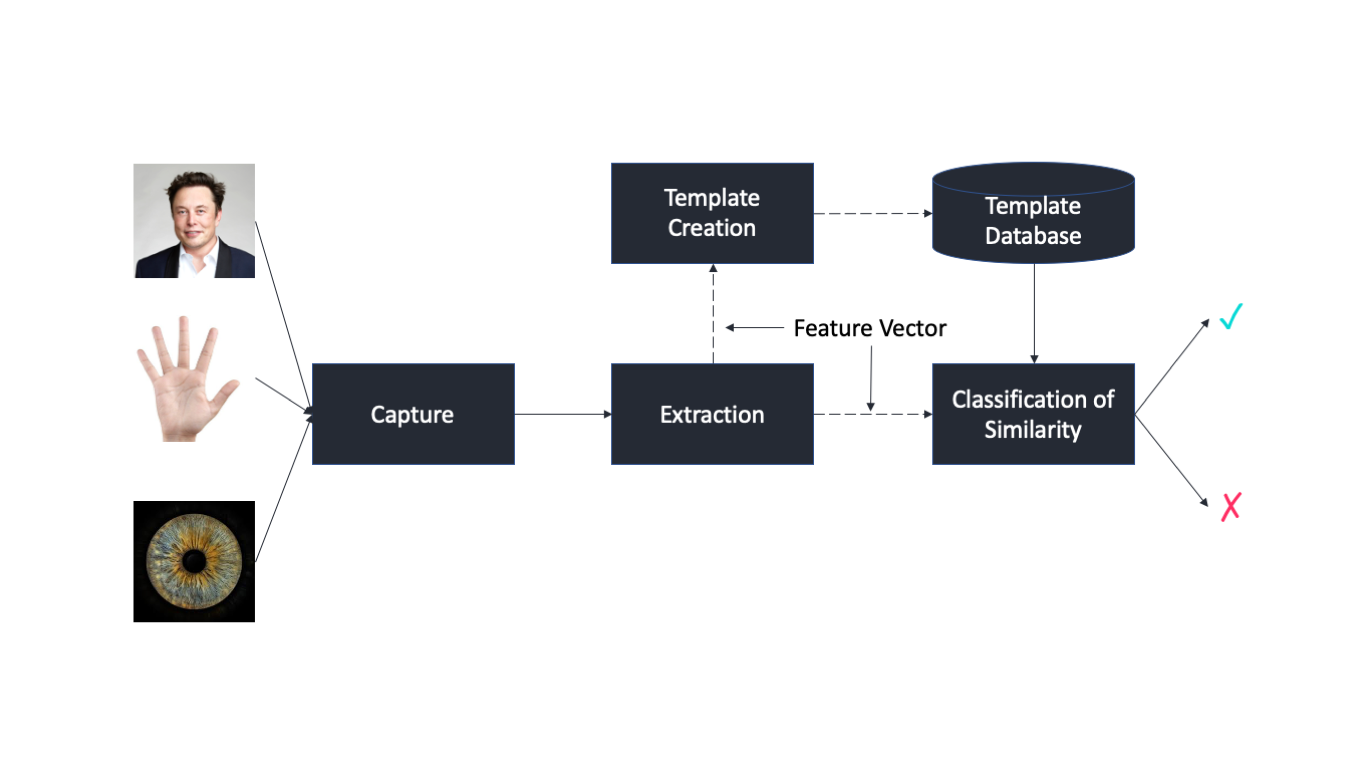
. Biometrics are body measurements and calculations related to human characteristics. Fingerprints and handprints are the most widely used biometric method in use today. A voiceprint is a set of measurable characteristics of a human voice that uniquely identifies an individual.
This biometric information can be used to verify identity when using other services. The smartcard is used for the first layer of mutual authentication when a user requests transaction. The means used to confirm the identity of a user process or device eg user password or token.
These characteristics which are based on the physical configuration of a speakers mouth and throat can be expressed as a mathematical formula. A smartcard based ATM fingerprint authentication scheme has been proposed. 4 Authentication using two or more factors to achieve authentication.
Biometric identifiers are the distinctive measurable characteristics used to label and describe. Are have been traditionally used for identification and authentication. Some of the biometric methods that can be used are fingerprints hand geometry retinal or iris scans handwriting and voice analysis.
Image Signal processing used to process fingerprint images. The possession smartcard together with the claimed users Biometrics fingerprint is required in a transaction. Fingerprint recognition is one of the most well known biometrics and it is by far the most used biometric solution for authentication on computerized systems.
The data can be unlocked whenever required and used for verification before you lock it again. TACACS is an encryption protocol and therefore less secure than the. CNSSI 4009-2015 under authenticator from NIST SP 800-53 Rev.
Discover the convenience of using the biometric payment card by watching. Many laptops include fingerprint readers and. The company says ATO attacks have ballooned over 307 percent on its network between April 2019 and June 2021 and are.
The detailed criteria used to answer these questions depend on the type of multi-factor authentication mechanism used. SHALL be generated by an approved random bit generator SP 800-90Ar1 and contain at least 64 bits of entropy. These are what are stored in the Biometric template.
I something you know eg. Biometric authentication or realistic authentication is used in computer science as a form of identification and access control. Biometric authentication is the second layer.
Passwordpersonal identification number PIN. Biometric methods provide the something you are factor of authentication. Individuals can avoid their Aadhaar card being mishandled by simply locking their biometric data that is stored on the UIDAI servers.
The idea is that you know something that is. Steps to Locking Aadhaar Biometric Data Online. They leverage the concept of possessing something that no one else does and which can help distinguish you from others.
The reasons for fingerprint recognition being so popular are the ease of acquisition established use and acceptance when compared to other biometrics and the fact that there are numerous ten sources of this. Fingerprint biometrics on cards is on the rise. This is one of the most commonly used algorithms for extracting features that characterizes a fingerprint.
It is also used to identify individuals in groups that are under surveillance. When a biometric factor is used in authentication at AAL2. Two Factor Authentication gives the user and system administrator a peace of mind as it ensures that even if the users password is compromised the account cannot be accessed without also knowing not only the method used as the second factor but also having access to the second factor such as a dynamically generated one-time password OTP or biological token.
They use it for both small and large amounts without the need to touch the terminal or enter a PIN code. In digital space this responsibility is born by passwords PINs security questions etc. Sift accentuates the need for improved security on its app gallery due to incidences of account takeover ATO attacks that have grown in recent years.
TSA is carrying out integration testing for a new form factor of Credential Authentication Technology CAT II devices provided by Idemia at its lab while also running pilots at three locations to validate a final set of requirements and determine operational procedures Lim revealed. Biometric Authentication Biometric. SHALL be erased or invalidated by the session subject when the subscriber logs out.
Solutions that do not align to SP 800-63-3 or which. The biometric authentication service will be available in the second quarter of 2022 Sift says. Many people have used the biometric payment card since its commercial launch in 2021 and enjoy its ease of use and security when making everyday payments.
The different Minutiae feature locations and types can identify different individuals. TACACS Terminal Access Controller Access Control System is an older authentication protocol common to UNIX networks that allows a remote access server to forward a users logon password to an authentication server to determine whether access can be allowed to a given system. SHALL be generated by the session host during an interaction typically immediately following authentication.
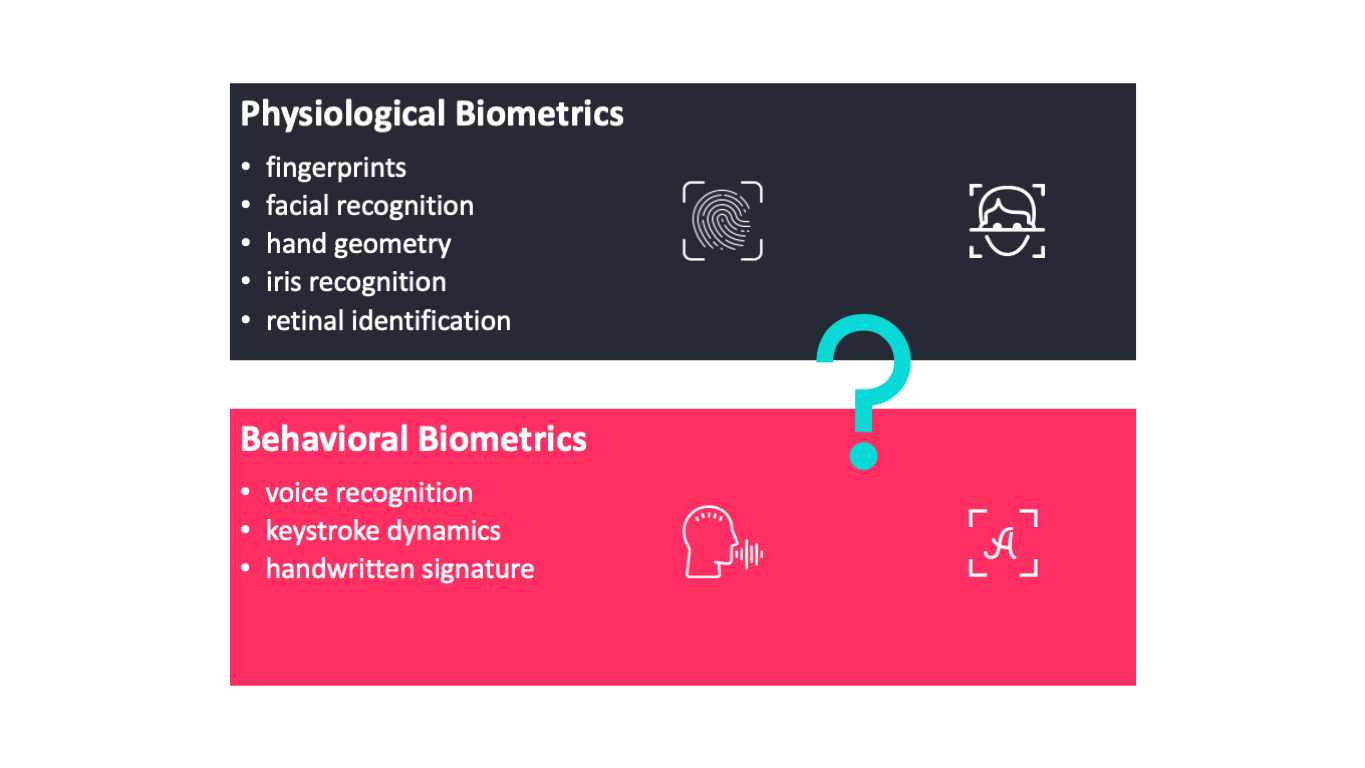
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

What Is Biometrics Authentication Types Of Biometrics And Trends
0 Response to "Which of the Following Is Used for Biometric Authentication"
Post a Comment